CyberNews 2-19-25
Cybersecurity News for Feb 19, 2025
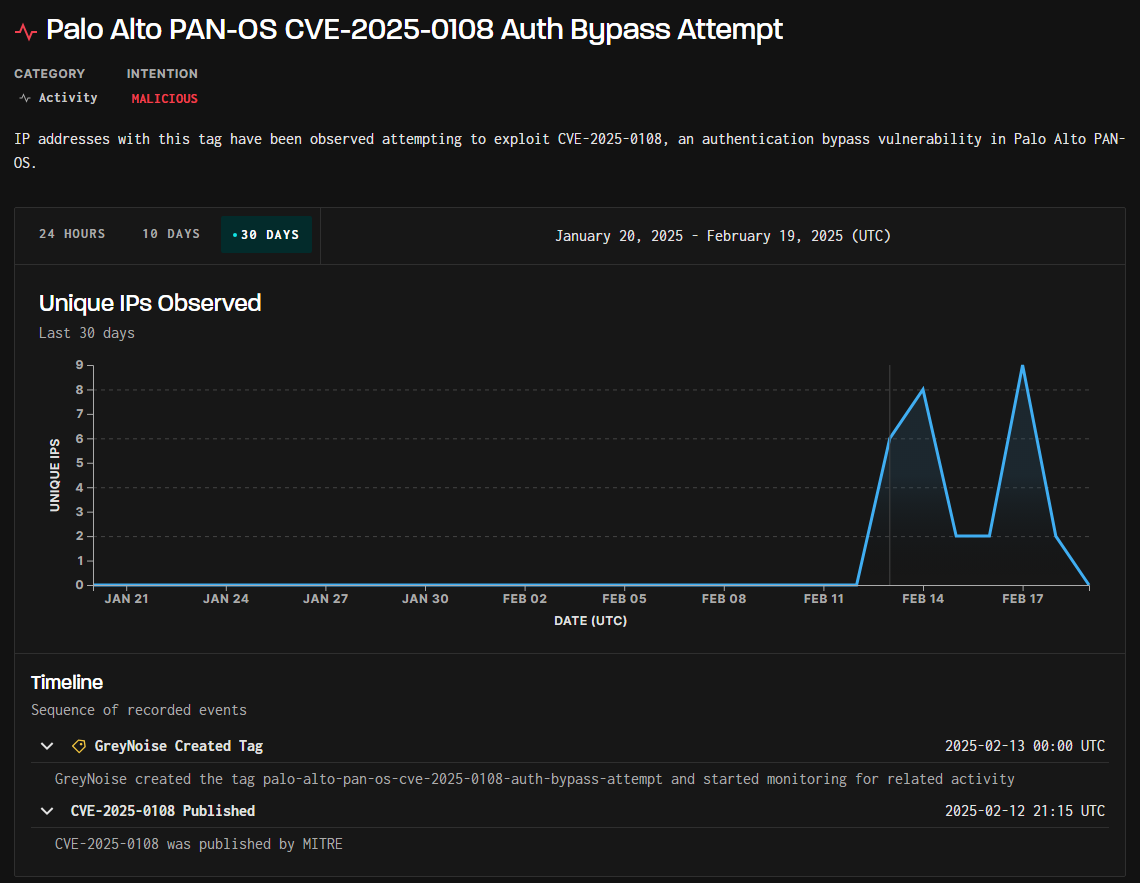
Story 1: ⚠️PAN-OS Vulnerability Actively Exploited in the Wild⚠️
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding the active exploitation of a high-severity authentication bypass vulnerability (CVE-2025-0108) in Palo Alto Networks’ PAN-OS. This flaw allows unauthenticated attackers to bypass authentication controls and execute specific PHP scripts, potentially compromising system integrity. Organizations using affected PAN-OS versions are strongly advised to apply the latest patches and restrict management interface access to trusted internal IP addresses. The EPSS Score for these vulnerabilities is -
EPSS Score for CVE-2025-0111 0.04%
Paloalto Security Advisory: CVE-2025-0111 PAN-OS: Authenticated File Read Vulnerability in the Management Web Interface
EPSS Score for CVE-2025-0108 0.04%
Paloalto Security Advisory: CVE-2025-0108 PAN-OS: Authentication Bypass in the Management Web Interface
EPSS Score for CVE-2024-9474 97.48%
Paloalto Security Advisory: CVE-2025-0108 PAN-OS: Privilege Escalation (PE) Vulnerability in the Web Management Interface
Read More
Story 2: SonicWall SonicOS SSLVPN Zero-Day Actively Exploited
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning about a critical zero-day vulnerability (CVE-2024-53704) in SonicWall’s SonicOS. This flaw allows remote attackers to hijack active SSL VPN sessions without credentials and is currently being exploited in the wild. CISA mandates that federal agencies patch affected systems by March 11, 2025, and recommends immediate remediation for all organizations using SonicWall devices.
- EPSS Score for CVE-2024-53704 0.05%
Story 3: Juniper Networks Patches Critical Authentication Bypass
Juniper Networks has released patches for a critical vulnerability (CVE-2025-21589) affecting its Session Smart Router (SSR) devices. Discovered during internal security testing, this flaw allows network-based attackers to bypass authentication and gain administrative control over the devices. Administrators are advised to update to the latest firmware versions to secure their networks against potential exploits.
- CVSS v3.1 Score for CVE-2025-21589 9.8
- CVSS v4 Score for CVE-2024-53704 9.3
Story 4: OpenSSH Fixes Flaws Enabling MitM and DoS Attacks
OpenSSH has addressed two vulnerabilities that could facilitate man-in-the-middle (MitM) and denial-of-service (DoS) attacks. Researchers from Qualys identified these flaws, which, when combined, could allow attackers to bypass server key verification in OpenSSH clients. Users are encouraged to update their OpenSSH installations to prevent potential exploitation.
Story 5: Ransomware Attack Shuts Down Five Michigan Casinos
A ransomware attack has forced the closure of five Kewadin Casinos across Michigan, affecting locations in Manistique, Hessel, St. Ignace, Christmas, and Sault Ste. Marie. While hotels remain open to current guests, new check-ins are suspended. The Sault Tribe of Chippewa Indians, which operates the casinos, is working with third-party experts to restore systems and investigate the breach.
Story 6: Chinese Hackers Exploit Microsoft App-V Tool to Evade Detection
The Chinese advanced persistent threat group “Mustang Panda” has been observed abusing Microsoft’s Application Virtualization (App-V) Injector utility to inject malicious payloads into legitimate processes. This technique helps the attackers evade detection by antivirus software. The group primarily targets government entities in the Asia-Pacific region through spear-phishing campaigns.
Story 7: Weaponized PDFs Deliver Lumma InfoStealer to Educational Institutions
A new campaign targeting educational institutions involves the distribution of weaponized PDF documents embedded with Lumma InfoStealer malware. These malicious PDFs contain LNK files that, when executed, initiate a multi-stage infection process to steal sensitive data. Educational organizations are advised to implement robust cybersecurity measures to defend against such threats.
Story 8: New Snake Keylogger Variant Targets Windows Systems
A new variant of the Snake Keylogger malware is infecting Windows users, particularly in Asia and Europe. This version utilizes the AutoIt scripting language to deploy itself, adding obfuscation layers to evade detection. Once installed, it logs keystrokes, captures screenshots, and steals clipboard data, compromising user credentials and sensitive information.
Story 9: Venture Capital Firm Insight Partners Suffers Cyberattack
New York-based venture capital and private equity firm Insight Partners has disclosed a cyberattack on its systems. The breach, resulting from a sophisticated social engineering attack on January 16, 2025, prompted the firm to engage third-party cybersecurity experts and notify law enforcement. While the investigation is ongoing, there is no evidence of continued unauthorized access.
Enjoy Reading This Article?
Here are some more articles you might like to read next: